Because the Azure RemoteApp client authenticates against Azure Active Directory (AAD) we are also able to leverage Conditional Access and Multi Factor Authentication (MFA) based on AAD. The RDS Product team also recently announced this in the blog post Control access to Azure RemoteApp with Azure AD Conditional Access!
In this blog post I’ll guide you through the process of setting up MFA on Azure RemoteApp.
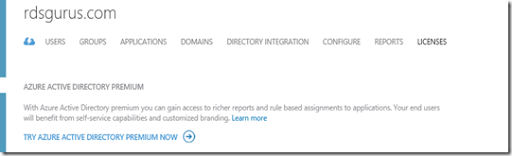
First of all, Conditional access requires Azure AD Premium (currently in preview). You can however set this up in a 30 day trial. To do that, open the Azure Portal browse to your AAD and choose the option “TRY AZURE ACTIVE DIRECTORY PREMIUM NOW”
Confirm the agreement below

It take a few minutes to setup. Click the refresh link to be able to start using it.

Shortly followed by that, you should receive a confirmation email that the organization is ready for Azure AD Premium.

To configure MFA, reopen the Azure Portal, go to Active Directory open your AAD domain en choose Applications.

Now click on Microsoft Azure RemoteApp and go to the Configure tab. For this demo, we’ll select Enabled Access Rules, have it applied to all users, and select Require multi-factor authentication.

The next time we log on to the Azure RemoteApp client with an organization account from this AAD, we are presented with the following;

This is MFA kicking in. We click “Set it up now”. And without having to leave the Azure RemoteApp client, we’re being presented the ability to provide a phone number and verification type that we would like to use for this account. In this case I choose Phone Authentication, and provide my cell number. (we obviously only have to perform these steps once).
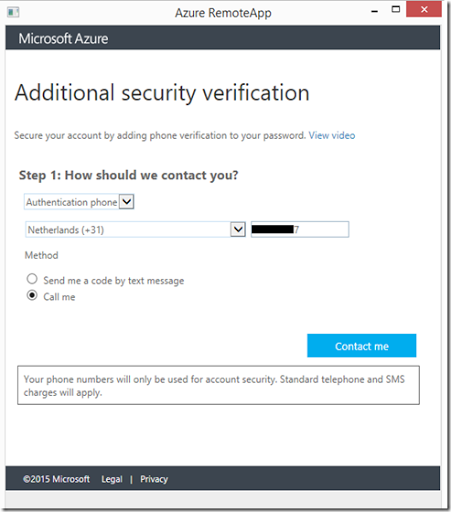
When we click Contact me, Azure MFA will call me on the number provided to verify the correct number.
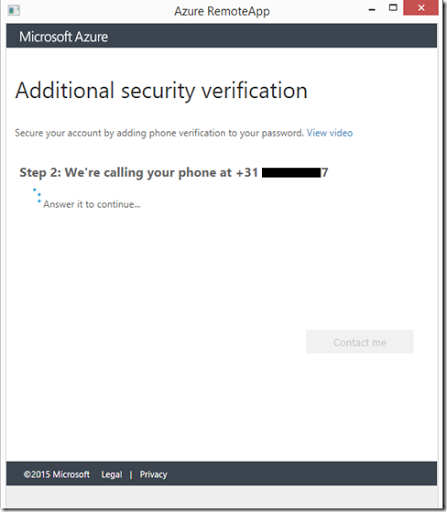
The verification process is now completed and we are ready to use MFA for Azure RemoteApp.

When proceeding the logon in the Azure RemoteApp client we’re presented with the following screen indicating that we can expect a call to our provided phone number to perform the MFA !
And after that, we’re presented with the RemoteApps assigned to us based on the Azure RemoteApp Collection.

There are some other options in conditional Access policy worth mentioning. We can for example specify to only enforce MFA when people are connecting from outside of the corporate (trusted) locations, or even block access in those cases.
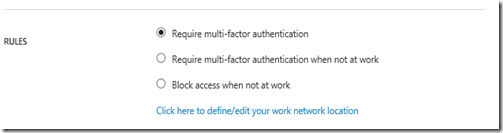
By clicking the link, we’re able to configure these trusted locations, configure whether or not we want to allow app passwords and even allow users to suspend multi factor authentication from remembered devices.

